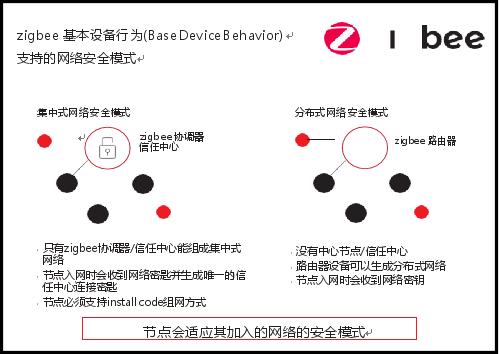
Since 2002, the Zigbee Alliance and its member companies have been working to create standards, certification programs, and testing tools for building interoperable products for low-power wireless Internet of Things (IoT). The number of devices using the zigbee standard to date has exceeded one billion worldwide. We fully understand that the security environment is constantly changing, so we provide our members with a complete set of security tools for their products. With the zigbee 3.0 standard (now referred to as zigbee) released in early 2016, we offer enhanced security tools for product developers and different vendors in the IoT ecosystem to build a stronger network and network security. Make appropriate trade-offs between ease of deployment and ease of deployment. The zigbee alliance keeps a close eye on industry security trends and is constantly updating with researchers and "white people" to ensure they are ahead of emerging threats. Based on the Alliance's award-winning zigbee PRO mesh network protocol, the zigbee solution features a number of new security features designed for today's market and evolving risk environments, including security features originally developed for the zigbee Smart Energy smart energy standard. The function has been applied to hundreds of millions of meters around the world, and no security holes have been found so far. Our industry-leading security tools, in partnership with leading wireless security experts, have helped our members develop some of the most secure wireless devices to date. These new features include: Device unique authentication when entering the network Key update during network operation Air firmware upgrade (OTA) security measures Connection-based logical encryption Safe mode In order to adapt to different application scenarios and ensure the best balance between security, ease of use, cost effectiveness and battery life, zigbee offers two network architectures and corresponding security modes: distributed network and centralized network, two The difference between them is that they solve the basic needs of the IoT network in different ways: how to get new devices to join the network and how to protect the messages transmitted on the network. (1) The distributed security mode system is relatively easy to configure, including two types of devices: routers and terminal devices (see the figure below). If the zigbee router does not detect an existing network at startup, it can autonomously generate a distributed security network. In a distributed network, any router can send a network security key (network key, network message's encryption key, translator's note). As more routers and end devices join the network, routers already on the network send network keys in a secure manner. All devices on the network use the same network key to encrypt messages. (2) The centralized system has higher security, including a third type of device - Trust Center, which is usually implemented in the network coordinator (see the figure below). The TC forms a centralized network, and only the routers and terminal devices are allowed to join the network when they have the relevant certificates. In a centralized network, the TC is the device that issues the encryption key. The TC also issues a unique TC Link Key when each device (or pair of devices) enters the network. Layered security settings The best security mechanism should use a layered approach from the physical layer to the application layer. Although the physical layer security settings are beyond the scope of the zigbee standard, the Alliance has been helping our members communicate with each other on best practices in this area. From the perspective of the protocol/standard, both the network layer and the application layer can provide security methods (including the process when entering the network). At the network layer, all devices are in a consistent security environment. Install codes (no suitable translation, translator's note) The TC can require each new device to join a centralized secure network with a unique Install Code. The Install Code must match the password that was previously entered into the TC in an out-of-band manner (ie, not through the zigbee network). For example, the Install Code can be printed in a package that is added to the device in digital or QR code; the user or installer can type or scan the password into a smartphone or tablet connected to the TC. All zigbee devices must contain a unique Install Code, which is a random 128-bit number protected by a 16-bit CRC. Joining devices and TCs use the Matyas-Meyer-Oseas (MMO) hash algorithm to generate a unique 128-bit Trust Center Link Key based on their common Install Code. For Oppo Glass,Oppo Find X3 Front Glass,Oppo Phone Screen Glass,Oppo Reno 5 Pro Glass Dongguan Jili Electronic Technology Co., Ltd. , https://www.jlocaglass.com