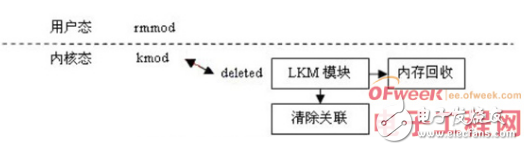
1 Introduction The Linux system has open source code and fewer system vulnerabilities, and can provide better security and stability in the face of viruses and hackers. Based on the above advantages, the application and research of Linux operating system and related technologies have been increasing in recent years. more. It takes a lot of time to recompile the kernel to expand or tailor the functions of the Linux operating system. Because the LKM mechanism greatly shortens the development and testing time, it plays a pivotal role in the process of Linux development and research. LKM mainly includes two functions of loading and unloading kernel modules in the operating system. Kernel modules are code blocks that can be loaded into the kernel to execute when the operating system kernel needs to be started, and unloaded by the operating system when not needed. They extend the functionality of the operating system kernel without the need to recompile the kernel and start the system. If there is no kernel module, you have to repeatedly compile and generate the kernel image of the operating system to add new functions. When there are many additional functions, the kernel will become bloated. 2. Writing and Compiling of LKM 2.1 The basic structure of the kernel module A kernel module contains at least two functions, the initialization function init_module() and the module that are executed when the module is loaded The end function cleanup_module() executed when it is uninstalled. In the latest stable version of the kernel 2.6, the two functions can start Arbitrary names are implemented through the macros module_init() and module_exit(). The only thing to note is that the function must be defined before the macro is used. E.g: staTIcint__inithello_init(void){} staTIcvoid__exithello_exit(void){} module_init (hello_init); module_exit (hello_exit); The purpose of declaring the function as staTIc here is to make the function invisible outside the file. The function of __init is to recover the memory occupied by the function after initialization. The macro __exit is used to ignore the end function when the module is compiled into the kernel. These two macros are only for the case where the module is compiled into the kernel, and are invalid for dynamically loaded modules. This is because the modules compiled into the kernel are not cleaned up and finished, but dynamically loaded modules need to complete these tasks by themselves. 2.2 Compilation of kernel modules When compiling, a makefile needs to be provided to hide a large number of complex operations at the bottom, so that the user can complete the task of compiling through the make command. The following is a simple makefile to compile hello.c: obj-m+=hello.ko KDIR:=/lib/modules/$(shelluname-r)/build PWD:=$(shellpwd) default: $(MAKE)-C$(KDIR)SUBDIRS=$(PWD)modules After compilation, the loadable module file hello.ko is obtained. Kernel version 2.6 uses the .ko file suffix instead of .o, which is to distinguish it from ordinary executable files. 3. The main functions of LKM 3.1 Module loading There are two ways to load modules. The first is to use the insmod command to load, and the other is to request the kernel background process kmod to load the appropriate module when the kernel finds that a module needs to be loaded. When the kernel needs to load a module, kmod is awakened and modprobe is executed, passing the name of the module to be loaded as a parameter. modprobe loads the module into the kernel like insmod, the difference is that when the module is loaded, it checks to see if it involves any symbols that are not currently defined in the kernel. If there is, search in other modules in the current module path. If found, they will also be loaded into the kernel. But in this case using insmod will end with the "unresolved symbol" message. About module loading, you can use Figure 3.1 to briefly describe: The insmod program must find the required kernel modules to be loaded. These kernel modules are linked object files. Unlike other files, they are linked into a relocatable image, that is, the image is not linked to a specific address. Insmod will execute a privileged system call to find the kernel's output symbols, which are stored in pairs with symbol names and numerical values ​​such as address values. The kernel output symbol table is stored in the first module structure of the module linked list maintained by the kernel. Only special symbols are added, and they are determined when the kernel is compiled and linked. insmod reads the module into virtual memory and modifies the reference addresses of unresolved kernel functions and resources by using kernel output symbols. These tasks are carried out by directly writing the address of the symbol into the corresponding address in the module by the insmod program. After insmod modifies the module's reference to the kernel output symbols, it will use the privileged system call again to apply for enough space to accommodate the new module. The kernel will allocate a new module structure and enough kernel memory to save the new module, and insert it into the end of the kernel module list, and finally mark the new module as UNINITIALIZED. insmod copies the module to the allocated space. If the kernel memory allocated for it has been used up, it will apply again, but the module must be loaded at different addresses if it is loaded multiple times. In addition, this relocation work includes the use of appropriate addresses to modify the module image. If the new module also wants to output its symbols to the system, insmod will construct an output symbol mapping table for it. Each kernel module must contain module initialization and termination functions, so in order to avoid conflicts, their symbols are designed not to be output, but insmod must know these addresses so that they can be passed to the kernel. After all these tasks are completed, insmod will call the initialization code and execute a privileged system call to pass the module's initialization and termination function addresses to the kernel. When a new module is loaded into the kernel, the kernel must update its symbol table and modify the old modules used by the new module. Those modules that depend on other modules must maintain a linked list of references at the end of their symbol table and point to it in their module data structure. The kernel calls the initialization function of the module, and if it succeeds, the module will be installed. The end function address of the module is stored in its module structure and will be called by the kernel when the module is unloaded. The state of the module is finally set to RUNNING. 3.2 Uninstallation of modules The module can be deleted using the rmmod command, but the requested load module will be automatically deleted by the system when its use count reaches 0. kmod executes a system call every time its idle timer expires and deletes all unused request load modules in the system. Regarding module uninstallation, it can be described in Figure 3.2: Modules that are still in use in other parts of the kernel cannot be uninstalled. For example, if multiple VFAT file systems are installed in the system, the VFAT module cannot be uninstalled. Executing lsmod will see the reference count of each module. The reference count of the module is stored in the first constant word of its image, which also contains the autoclean and visited flags. If the module is marked as autoclean, the kernel knows that the module can be uninstalled automatically. The visited flag indicates that this module is being used by one or more file system parts, and this flag is set as long as there are other parts using this module. Every time the system deletes unused request load modules, the kernel will scan all modules, but generally only check those modules that are marked as autoclean and are in the running state. If the visited mark of a module is cleared, it will be deleted. Other modules that depend on it will modify their respective reference domains, indicating that the dependencies between them no longer exist. The kernel memory occupied by this module will be reclaimed. 4. Application of LKM The basic idea of ​​zero copy is: in the process of data packet transfer from network equipment to user program space, reduce the number of data copies, reduce system calls, realize zero participation of the CPU, and completely eliminate the load of the CPU in this respect. The realization of zero copy is divided into two parts: realizing DMA data transmission and address mapping. Among them, DMA data transmission has little to do with this article, so I won't describe it in detail. Here we mainly introduce the address mapping realized by the LKM mechanism. The basic principle of address mapping is to apply for memory in the kernel space, and map it to the user space through the proc file system and mmap function to allow application access, thus eliminating the data copy from the kernel space to the application space. The realization of the address mapping part is mainly divided into the following three steps: First, establish the basic structure of LKM, including writing initialization and termination functions. Second, declare the functions required to complete the mapping function, mainly including the allocation and initialization of the kernel memory function init_mem(), the release of the kernel memory function del_mem(), and the function put_mem() for inputting content to the kernel memory. Third, in the initialization function, use the function established in the second step to allocate a memory space, input content, and establish a proc file system entry. Release the allocated kernel memory in the end function and delete the proc file system entry. Write an application program to test the LKM, and found that the purpose of mapping the kernel memory to the application program space has been achieved. In the process of realizing zero copy, the LKM mechanism is not only convenient for debugging, but also greatly reduces the development time. 5. Comparison of LKM and ordinary applications The difference between LKM and ordinary applications is mainly reflected in four aspects. The first and most important difference is that ordinary applications run in user space, while LKM runs in kernel space. By distinguishing different operating spaces, the operating system can safely protect the contents of some important data structures in the operating system from being modified by ordinary applications, so as to ensure the normal operation of the operating system. Second, the goal of ordinary applications is very clear, they are from beginning to end to complete a specific task. The LKM is registered in the kernel and provides services for subsequent application requests. Third, ordinary applications can call functions that are not defined in it, but an LKM is linked to the kernel, and the only functions it can call are those exported by the kernel. Fourth, common applications and LKM handle errors in different ways. When there is an error in the application, it will not cause great harm to the system. This is not the case with LKM, where errors are usually fatal to the subsystem, at least for the currently running process. An error in LKM often causes the entire system to crash. 6. Issues that need to be paid attention to when writing LKM LKM runs in the kernel space and they have access to all resources of the entire system. Therefore, the first thing to pay attention to when writing LKM is the security issue, and you should also avoid bringing code that may cause security issues to LKM. After LKM is loaded, it runs as a part of the operating system kernel. Therefore, the problems that should be paid attention to in the process of designing and writing the operating system kernel should also attract enough attention in LKM. Here, it mainly refers to the concurrency problem and the pointer reference problem. Concurrency refers to multiple processes running in the operating system kernel at the same time. Concurrency combined with shared resources will eventually lead to race conditions. In this case, access to shared resources by each concurrent process should be strictly controlled. If a pointer reference error occurs in the LKM, the kernel will have no way to map the virtual address of the memory to the physical address, which will cause accidents in the kernel, such as memory access conflicts, division by 0, and illegal operations. 7. Shortcomings of LKM Although LKM plays a very important role in the writing of device drivers and the expansion of kernel functions, it still has many shortcomings. First, LKM is too dependent on the kernel version. Each LKM is organized by the functions and data structures provided by the kernel. When these kernel functions and data structures change due to kernel version changes, the original LKM may not function properly without modification. Second, although there is a tool kgdb for kernel programming and debugging, debugging is still very troublesome in the process of writing LKM, and during the debugging process, the error information that the system can provide is extremely obscure. Innovation point: For the Linux kernel, using LKM, in the process of realizing zero-copy of data (Zero-copy), comparing LKM with ordinary applications, and proposing the advantages and disadvantages of LKM. 1.25mm Wire To Board Connectors
1.25mm Wire To Board Connectors are avialable in different terminations and sizes intended for use on a variety of applications. These connectors provide power and signal with different body styles, termination options, and centerlines. To find the wire to board set required, click on the appropriate sub section below.
Description Automotive Connectors,1.25Mm Wire To Board Connectors,1.25Mm Pcb Wire To Board Connector,1.25Mm Pin Wire To Board Connector,.049" Pitch Wire To Board Connectors ShenZhen Antenk Electronics Co,Ltd , https://www.pcbsocket.com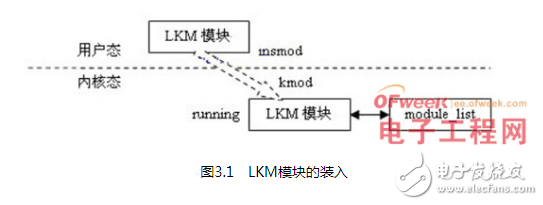
1.25mm wire-to-board connector system is designed for a wide variety of applications in Industrial, Automotive, and Consumer markets.
The comprehensive range consists of terminals, crimp housings and PCB headers in straight and right angle, surface mount and through-hole configurations. It is available in 2 to 15 circuits in a single row. 1.25mm wire-to-board solution conforms to the EU Industry Safety Standard. PCB header material meets halogen-free requirements and can be operated in the temperature range from -40°C to +105°C.
Saves space with a 1.25mm pitch
Suitable for Industrial, Automotive, and Consumer markets
Crimp housing with friction feature
Conforms to EU Industry Safety Standard
Accommodates wire range up to 32AWG-28AWG
Features
Three plating versions - Tin 15μin Gold, 30μin Gold and Gold Flash
Fully polarized housings
Crimp housing with friction feature
Tape and Reel packaging with pick up cap
UL94V-0 flammability rated LCP material
Halogen-free resin material
RoHS compliant and lead-free
Benefits
Supports applications in a wide range of environments
Prevents accidental mismating
Provides additional retention and prevents harness-to-header mismating
Pick and place for SMT production process
High flammability rating
Meets environmental requirement
Meets environmental, health and safety requirement
Applications
Consumers
Car Audio
Industrial & Instrumentation
Industry Control
Instrumentation/Metering
Office Equipment
Small Motor/Robot Control
Security
Alarm Systems
Vending POS Machine