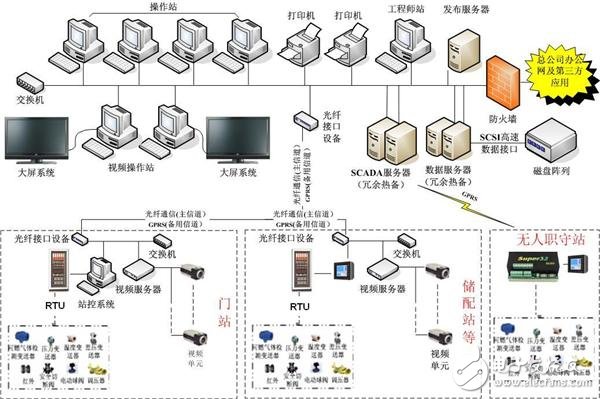
At present, the network threats against circuit transmission networks are rapidly upgrading, especially for SCADA systems, and it is becoming more and more common. It is almost impossible to defend against every "state of the art" cyberattack, so the "containment" measure is very important. According to a recent report from Dell Security, the number of cyberattacks for data acquisition and surveillance control (SCADA) systems has nearly doubled last year, and the number of cyberattacks for SCADA systems has increased compared to 2012. Nearly six hundred percent. Although the data is amazing, another key research result is even more disturbing, and physical destructive attacks are becoming more common. In fact, in all of the cybersecurity incidents last year, 25% of cyberattacks were directed at SCADA systems. These specific types of attacks were able to shut down mechanical devices in industrial systems and potentially disrupt the physical entities of the devices. According to the researchers, such attacks will become even more serious in the next few months, even in the next few years. In addition, the United States will become the third country in the world to be most affected by such attacks. The US Department of Homeland Security's Industrial Control Systems Network Emergency Response Team (ICS-CERT) has similar findings. They have found that attacks on industrial critical infrastructure are growing, and the energy industry is the most affected of all types of attacks. (32% of all attacks). Moreover, denial of service (DoS) attacks have become the favorite of attackers. Why are such complex attacks becoming more frequent now? There are two main reasons: The first is hacking, hacking and foreign government collusion, and organized cybercrime. Second, the power company is the most important target of all groups. Considering various political factors, the attacker can profit from the attack. So in the next few years, such attacks will become more frequent and the consequences will become more and more serious. Stealthier attacks: The power company's IT team may be most familiar with "phishing" emails and "botnets" because they are the most vulnerable to their network systems. However, these attacks will escalate and then become more complex, purposeful and invisible. In general, organizations should pay special attention to the following two types of attacks: "cross-site scripting attacks" and "drive-by attacks." Both types of attacks use a legitimate website to invade a company's internal network, but we won't give you too much technical detail here. But how is this achieved? Because a vulnerability exists in a legitimate website (these websites can be a famous website, a new website, a technical forum, etc.) can allow an attacker to execute malicious code, and can also implant malware in the website. So you can infect any user who visits this site. The only condition required for a "drive-by attack" is the need for a company employee to access the infected website. In a cross-site scripting attack, when a company employee clicks on a legitimate link attached to an email, it is successfully infected. Attackers are also more inclined to attack the computer systems of a company employee's home. An attacker can steal user credentials stored on a home PC or infect a removable media storage device (such as a USB flash drive) because the employee is likely to bring the device to his workplace. Destructive malware (DestrucTIve malware): Malware is constantly evolving, and now there are more devastating malware that we have never seen before. Many people may be familiar with the name "Shenzhen." This is a complex worm. It is the world's first destructive virus specifically written for industrial control systems. It has already infected industrial systems in many countries and regions. And individual users. Of course, there are many other kinds of viruses, worms and Trojans that can disable some of the features of physical devices. The two most important parts are: "wipers", which erases all data on one computer or device, making the target device completely unusable; the other is "encrypted malware", it won't The data on the device is deleted, and the data in the device is encrypted using an encryption method that is almost impossible to crack. To put it bluntly, the purpose of encrypted malware is to "blackmail" users. Denial of service: In addition to malware that can disrupt the day-to-day operations of the factory, there are a number of web attacks that do the same. The two most common ones are: "buffer overflow", when an attacker floods the network, it will cause network system shackles; there is also a "distributed denial of service attack", which will utilize a large number of reasonable services. Requests to take up too much service resources, so that legitimate users can not get the response of the service, which causes the system to paralyze. The fact is that your factory is vulnerable to these types of attacks. According to the Department of Homeland Security, researchers have found these vulnerabilities to be the most common vulnerabilities in industrial facilities. Develop an effecTIved efense: As these attacks will become more and more complicated, it is even more important for the company's managers to concentrate their efforts on the loss management control measures after the attack event during their active cyber defense process. important. If you want to defend against every "state of the art" cyberattack, this is almost impossible, so the "containment" measure is equally important. Available defenses include security audits of outdated or unpatched systems, deployment of anti-virus software for personal workstations, web servers, and web applications. For example, is your network connected to a device running Windows XP or Windows Server 2003? You also need to install modern firewalls, malware detection tools, set up email whitelists, and set up firewalls that proactively monitor suspicious network activity, such as data leaks, in your industrial production environment. All removable/portable media storage devices are prohibited from entering the workplace – which means that all USB flash drives, smartphones, tablets and other devices are not allowed to enter the workplace. Containment measures after a security incident are also crucial. You need to ensure that all critical industrial systems have air gap systems. Then learn how to divide the network in the best way from other network systems. Network segmentation is critical because when a computer on the network is infected, it cannot infect the entire network system. You are also suspicious of adopting an "access control" strategy. A single company employee should not have excessive access to company data, systems, and key business operations. At the same time, you also need to check the program log records of your industrial system frequently. This is very important because any network events are fully documented so that the incident response team can determine the type of attack and the extent of the damage caused by the attack.
USB Charger
The Universal Serial Bus (USB) port on computers and laptops is a data port that also serves as a 5-volt power source.Virtually all portable, personal electronics feature a USB port, though the connector can vary between one of several standards. The charger plugs into an AC outlet, and a USB Cable plugs into the charger.
USB Charger,30W USB C Wall Charger,Fast Charging USB C Wall Charger,Ports 60W Wall Charger Home Charger Pogo Technology International Ltd , https://www.pogomedical.com